You arrive at the office, power up your system, and panic sets in. Every file is locked, and every system is frozen. A ransom demand flashes on your screen: “Pay $2 million in Bitcoin within 48 hours or lose everything.”
And the worst part is that even after paying, there’s no guarantee you’ll get your data back. Many victims hand over the money, only to receive nothing in return, or worse, get hit again.
This isn’t a rare case. Ransomware attacks are crippling businesses worldwide, from hospitals and banks to small companies. The only way to stop the damage is by proactively analyzing suspicious files and links before they can be executed.
Below, we break down the top three ransomware families active in 2025: LockBit, Lynx, and Virlock, and find out how interactive analysis helps businesses detect and stop them before it’s too late.
LockBit: Teasing a Comeback in 2025
LockBit is one of the most notorious ransomware groups, known for its highly efficient encryption, double extortion tactics, and ability to evade traditional security measures. Operating under a Ransomware-as-a-Service (RaaS)model, it enables affiliates to distribute the malware, leading to widespread attacks across various industries.
Latest attacks and activity:
- London Drugs (May 2024): LockBit targeted Canadian retailer London Drugs, forcing the closure of all its locations across Canada. Hackers demanded $25 million, leaking some employee data after the company refused to pay.
- University Hospital Center, Zagreb (June 2024): Disrupted Croatia’s largest hospital, forcing staff to revert to manual operations while attackers claimed to have exfiltrated medical records.
- Evolve Bank & Trust (June 2024): Breached sensitive financial data, with hackers falsely claiming to have Federal Reserve information. The attack raised concerns due to Evolve’s ties with major fintech firms.
LockBit sample:
Let’s take a closer look at a LockBit ransomware sample inside ANY.RUN’s secure sandbox to discover its key behaviors.
| File icons changed inside ANY.RUN sandbox |
Inside the Interactive Sandbox, we notice the first thing that stands out: file icons changing to the LockBit logo. This is an immediate sign of ransomware infection.
Uncover ransomware tactics in real-time and prevent costly breaches before they happen.
This is followed by a ransom note inside the sandbox, stating that your files have been stolen and encrypted. The message is clear: Pay the ransom, or the data will be published on a TOR website.
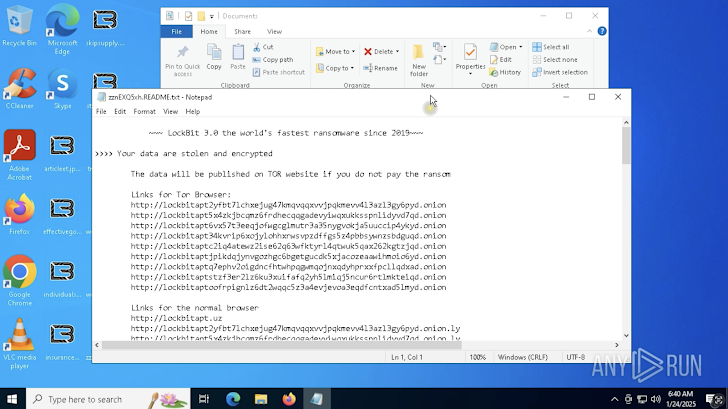 |
| Ransom note displayed inside secure environment |
On the right side of the screen, we see a detailed breakdown of every process LockBit executes to attack the system.
 |
| Process tree demonstrates the behaviors of LockBit |
By clicking on any process, security teams can analyze the exact tactics used in the attack.
 |
| Detailed breakdown of processes inside Interactive Sandbox |
This type of analysis is important for businesses as it allows them to understand how ransomware spreads, identify weak points in their security, and take proactive steps to block similar threats before they cause financial and operational damage.
For a more in-depth breakdown of the attack tactics, you can also click on the ATT&CK button in the upper-right corner of the sandbox. This provides detailed insights into each tactic, helping teams fine-tune their defenses and strengthen response strategies.
 |
| MITRE ATT&CK tactics and techniques detected by ANY.RUN |
In this case, we see LockBit using several dangerous techniques:
- Gaining higher privileges by bypassing security controls.
- Extracting stored credentials from files and web browsers.
- Scanning the system to gather information before encrypting files.
- Encrypting data to lock down critical business operations.
New attack warning in 2025:
Despite law enforcement actions, LockBit continues to pose a significant threat for 2025. The group’s alleged leader, known as LockBitSupp, has warned of new ransomware attacks launching this February. This means businesses cannot afford to let their guard down.
Lynx: The Rising Threat to Small and Mid-Sized Businesses
Lynx is a relatively new ransomware group that surfaced in mid-2024 and quickly built a reputation for its highly aggressive approach. Unlike larger ransomware gangs that focus on corporate giants, Lynx deliberately goes after small and mid-sized businesses across North America and Europe, taking advantage of weaker security measures.
Their strategy relies on double extortion. They don’t just encrypt files but also threaten to leak stolen data on both public websites and dark web forums if victims refuse to pay. This forces businesses into an impossible choice: pay the ransom or risk having confidential data, financial details, and customer records exposed online.
Latest Lynx attack:
In mid-January 2025, Lynx targeted Lowe Engineers, a prominent civil engineering firm based in Atlanta, Georgia. The attack led to the exfiltration of sensitive data, including confidential project information and client details. Given the firm’s involvement in critical infrastructure projects, this breach raised significant concerns about potential impacts on federal and municipal contracts.
Lynx sample:
Thanks to ANY.RUN’s Interactive Sandbox, we can analyze the full attack chain of Lynx ransomware in a controlled virtual environment, without risking real systems.
The moment we upload and launch the malicious executable file in ANY.RUN’s cloud-based sandbox, the ransomware immediately starts encrypting files and changes their extensions to .LYNX.
 |
| The Files Modification tab provides the changes of file system activity |
Shortly after, a ransom note appears, and the desktop wallpaper is replaced with an extortion message directing victims to a TOR site, where attackers demand payment.
 |
| Lynx ransomware changing the wallpaper inside ANY.RUN sandbox |
Inside the ANY.RUN sandbox, we can manually open the README.txt dropped by Lynx to view the ransom message exactly as a victim would.
 |
| The ransom note includes .onion links that direct victims to the attackers’ communication portal |
In the MITRE ATT&CK section, we get a clear breakdown of Lynx’s tactics and techniques, revealing how it operates:
 |
| MITRE ATT&CK tactics and techniques used by Lynx ransomware |
- Encrypting files to lock critical business data.
- Renaming files to mimic other ransomware strains.
- Querying the registry to scan for system details and security software.
- Reading CPU information to assess the target environment.
- Checking software policies to determine security settings before proceeding.
Virlock: A Self-Replicating Ransomware That Won’t Die
Virlock is a unique ransomware strain that first emerged in 2014. Unlike typical ransomware, Virlock not only encrypts files but also infects them, turning each into a polymorphic file infector. This dual capability allows it to spread rapidly, especially through cloud storage and collaboration platforms.
Recent attacks:
In recent analyses, Virlock has been observed spreading stealthily via cloud storage and collaboration apps. When a user’s system is infected, Virlock encrypts and infects files, which are then synced to shared cloud environments.
Collaborators who access these shared files inadvertently execute the infected files, leading to further spread within the organization.
Virlock sample:
Let’s analyze Virlock’s behavior using a real-time sample inside ANY.RUN’s sandbox.
View sandbox analysis of Virlock
 |
| Virlock ransomware inside VM |
Just like LockBit and Lynx, Virlock drops a ransom note upon execution. However, this time, it demands payment in Bitcoin, a common tactic among ransomware operators.
In this specific sample, Virlock asks for the equivalent of $250 in Bitcoin, threatening to permanently delete files if the ransom isn’t paid.
Interestingly, the ransom note doesn’t just demand payment. It also includes a guide on Bitcoin, explaining what it is and how victims can acquire it for payment.
 |
| Ransom note demanding BitCoin left by Virlock |
During execution, ANY.RUN detects several malicious activities, revealing how Virlock operates:
 |
| Behavior of Virlock ransomware analyzed by Interactive Sandbox |
- A Virlock-specific mutex is identified, helping the malware ensure only one instance runs at a time to avoid interference.
- Virlock executes commands through batch (.bat) files, launching CMD.EXE to perform malicious actions.
- The ransomware modifies the Windows registry using REG/REGEDIT.EXE, likely to establish persistence or disable security features.
Each sandbox session in ANY.RUN automatically generates a detailed report that can be easily shared within a company. These reports are formatted for further analysis, helping security teams collaborate and develop effective strategies to combat ransomware threats in 2025.
 |
| Generated report by ANY.RUN sandbox |
Ransomware in 2025: A Growing Threat You Can Stop
Ransomware is more aggressive than ever, disrupting businesses, stealing data, and demanding millions in ransom. The cost of an attack includes lost operations, damaged reputation, and stolen customer trust.
You can stop ransomware before it locks you out. By analyzing suspicious files in ANY.RUN’s Interactive Sandbox, you get real-time insights into malware behavior, without risking your systems.
Try ANY.RUN free for 14 days to proactively identify cyber threats to your business before it’s too late!










